Google Initiates Rollout of Enhanced Android Theft Protection Features
Google has commenced the rollout of its Android Theft Protection features, designed to provide users with an additional layer of security in the event of device theft. This new functionality is aimed at safeguarding personal data and preventing unauthorized access to stolen devices.
Theft Detection Lock
The Theft Detection Lock feature utilizes a combination of device sensors, Wi-Fi, and smart device connections to detect when a device is being taken without the owner's consent. If the system determines that the device is being stolen, the screen will automatically lock, thereby preventing access to personal data. This feature is triggered when the device is in use and unlocked, and the screen can be locked up to twice a day.
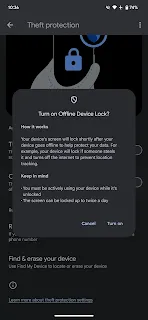
Offline Device Lock
In the event that a thief attempts to disable internet connectivity to prevent location tracking, the Offline Device Lock feature will be triggered. This feature requires two conditions to be met: the device must be actively in use while unlocked, and the screen can be locked up to twice a day.
Remote Lock
The Remote Lock feature allows users to remotely lock their device in the event of theft. By visiting android.com/lock, users can initiate the lock process by providing their phone number, which is confirmed during the setup process, and completing a security challenge. This feature can be accessed from another person's phone, providing a faster alternative to logging into Find My Device.
Availability
Google began testing these features in Brazil in June and has now started rolling them out to Android users worldwide, including those using Pixel and Samsung devices. However, it appears that this is not a full-scale launch, and not all users have access to the features yet. On our end, all three Theft detection capabilities are available when enrolled in the Google Play services beta (version 24.40.33), but not on the stable channel.
By introducing these enhanced Theft Protection features, Google aims to provide users with greater peace of mind and an additional layer of security for their personal data.



Comments
Post a Comment